
Workspace ONE Access will soon offer support FIDO2 Web Authentication( WebAuthN) on Windows 10 and MacOS devices. This means when logging into your Horizon Resources or any SAAS application that uses Workspace ONE Access, you can leverage Windows Hello, Touch ID, or Yubikey for authentication.
With this upcoming release, end users can self register their FIDO2 Authenticator (security keys or built-in platform authenticators) with Workspace ONE Access. Administrators can control the required level of authentication in order to register a FIDO2 Based Authenticator, such as Certificate + Device Compliance or Password + MFA. Once your FIDO2 Authenticator is registered, this can be used as either a primary or secondary factor.
Note: This is currently only supported in SAAS ONLY.
VMware is officially supporting the following Authenticators:
- Yubikey 5 NFC
- Yubikey 5c NFC
- Yubikey 5 Nano
- Yubikey 5c
- Yubikey 5c Nano
- Yubikey 5CI
- Windows Hello on Windows 10
- Touch ID on MacOS (Safari 14.0.2 or above)
Once you’ve enabled FIDO2 in Workspace ONE Access (along with True SSO) , you can provide a seamless user experience into your Horizon Desktop.
Enabling the Authenticator
- In Workspace ONE Access, go to Identity & Access Management-> Authentication Methods
- Enable the FIDO2 Authenticator

- Click Save
- In Identity & Access Management -> Identity Providers, click on your Built-in IDP
- Select the FIDO2 Authentication Method to associate it with your Built-in IDP

- Click Save
Setting up your Policies
In this section, we will walk through configuring the default policy for both registration and authentication. In your environment, you may have application policies in addition to the default policy. You may want to split out the registration of your FIDO2 Authenticator to the default policy and provide FIDO2 as an authentication method in your application policies. Note: The registration of your FIDO2 authenticator can only be on your default access policy.

- In the Workspace ONE Access admin console, go to Identity & Access Management -> Policies
- Select the “default access policy set” and click Edit.
Adding the Registration Policy Rule
- Click Add Policy Rule (You might have to scroll down if you have a lot of policy rules).
- Select All Ranges
- Select All Device Types. Note: Since this policy rule is for registration only, its easier to just make it available to all devices types. Alternatively, we can create two separate policy rules for Windows 10 and MacOS but I think its unnecessary. This policy is only triggered when someone clicks on “Register your FIDO2 Authenticator” from the sign-on screen that will only be displayed on MacOS & Windows 10.
- Select the slider for “and the user is registering FIDO2 Authenticator” to YES
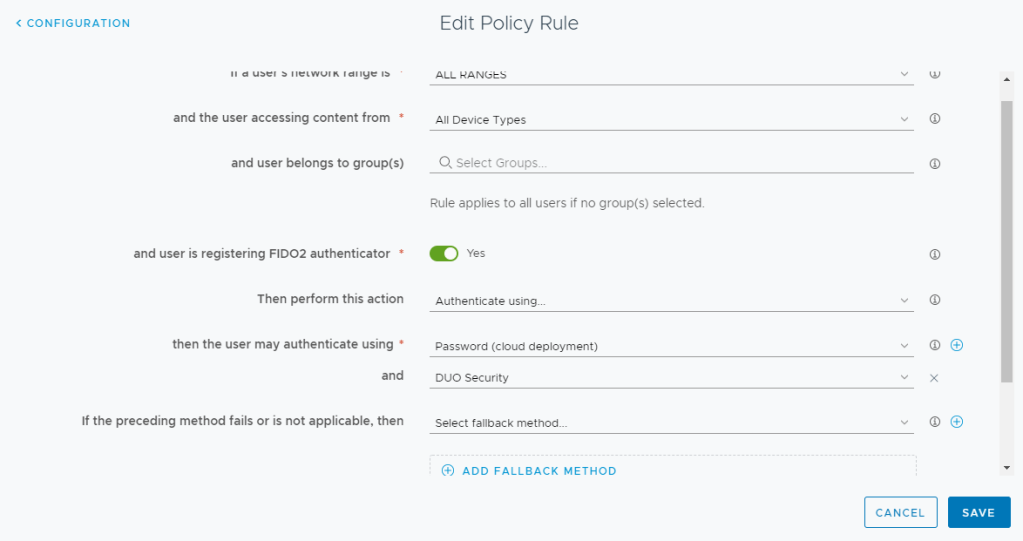
- Select the Authentication Methods that you want your users to use when registering their FIDO2 Authenticator. In my environment, I’m using Password + MFA in order to register a FIDO2 Authenticator. Note: If you don’t want to allow System Domain users, do not provide an option for Password (Local Directory) as this will allow system domain users to register a FIDO2 Authenticator.
- Click Save
Note: You may see issues on Firefox with FIDO2 registrations. This will improve as browsers improve their capabilities around FIDO2.
Adding the Authentication Policy Rule
- Click Add Policy Rule (You might have to scroll down if you have a lot of policy rules).
- Select All Ranges
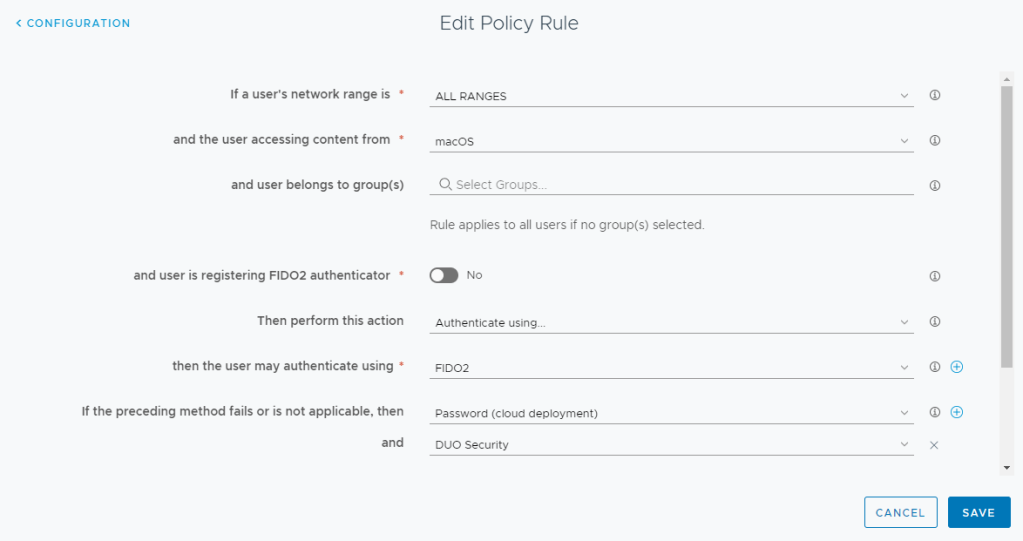
- Select MacOS
- Make sure the slider for “and the user is registering FIDO2 Authenticator” is set to NO.
- Select Fido2 for the first authentication method
- Select a fallback back Authentication Method in case Fido2 is not available. Users can chose this method by clicking on “Sign in another way” from the login Screen. In my example, I’m using Password + MFA.
- Click Save.
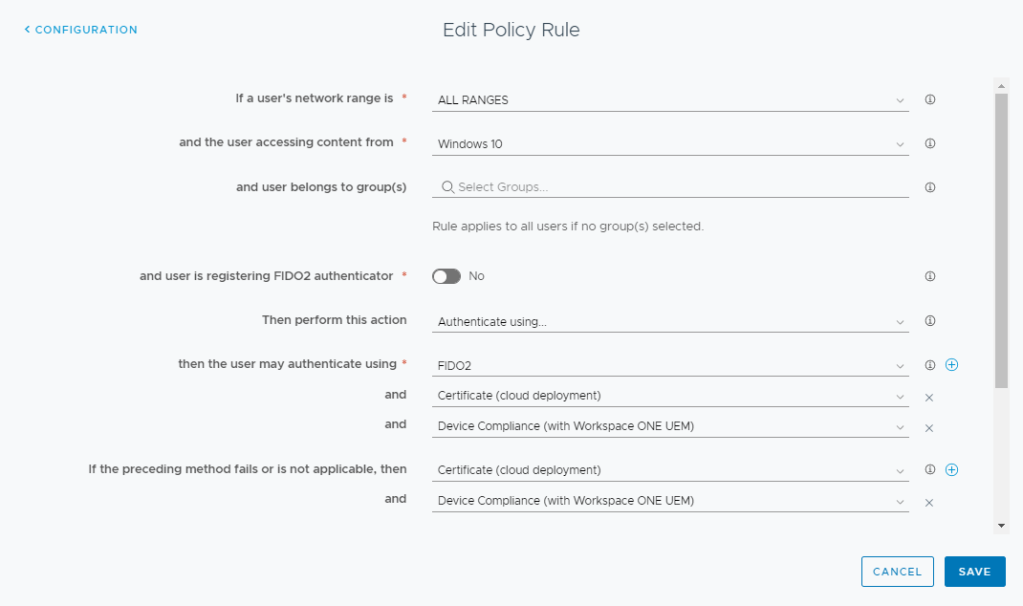
- Repeat these steps for Windows 10. In my example, I’m using Certificate Authentication as an alternative method of signing in.

- As alternate option, you can include both FIDO2 and Certificate Authentication with a Device Compliance Check
Ordering your Policy Rules
Ordering your policy rules is extremely important to make sure that everything works properly. The policy rule for registration needs to be before your Windows 10 and MacOS policy rules. You can see in my screenshot below that my registration rule (indicated by the device type ANY) is near the top:
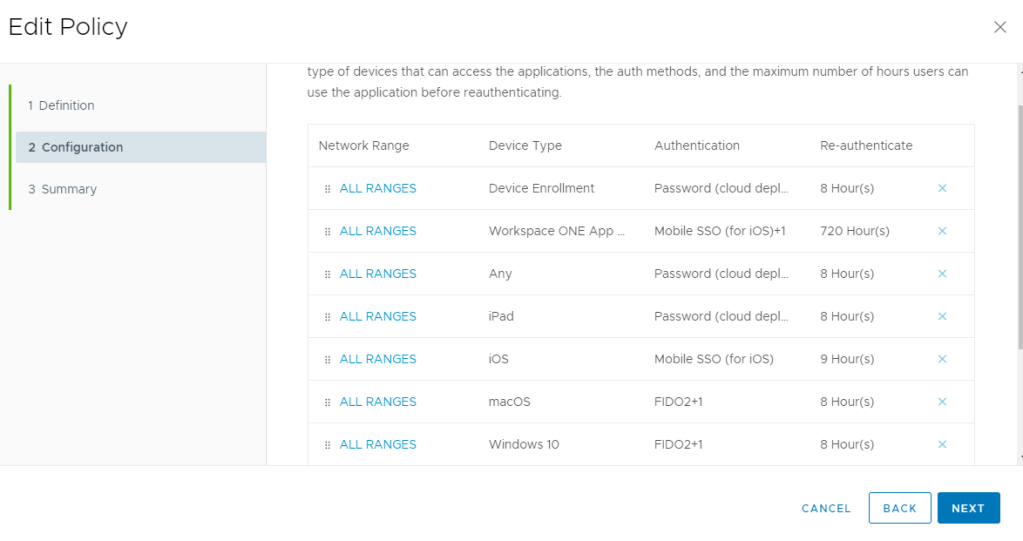
The MacOS and Windows10 policies can be anywhere below the registration policy.
Note: Chromium-based browsers have varying support for FIDO2 using incognito mode. In these cases, users will have to use the fallback authentication.
Administrative Management
Administrators can pre-add USB FIDO2 Authenticators (ie. Yubikey) into the system and maintain full life-cycle of the authenticators as well.

Using the Workspace ONE Access Admin Console, in a user profile, an admin can Add, Delete, Rename, Block or Unblock the USB Security Keys.
Hello Steve, we would like to tell you about our situation and the following questions:
For the immediate future we may have a solution based on VMware Horizon or Citrix VDA, but we will focus on Horizon to be more concrete. In this solution an on-premise WS1 authentication is proposed, and we have M365 licenses with its associated Azure AD services. On the other hand, we have Lenovo laptops with biometrics and Windows 10. We do not have Azure AD P1 licenses. We would like to have passwordless access to WS1 on premise. Do we need Windows Hello or just use Lenovo’s biometric device? Is it possible to use authentication with WS1 on-premises?
Is this passwordless authentication possible if a SAML query to Azure AD is required to validate user in our local AD? Microsoft tells us that to use WHFB from our EUC instance (VDI / RDSA) a “certificate trust” environment is needed and this requires Azure AD premium licenses.
Best regards, Steve
LikeLike
HI Lino – Currently the FIDO2/WebAuthN is only supported in our SAAS offering for Workspace ONE Access. The FIDO2 WebAuthn uses the platform authenticators to leverage Windows Hello functionality. I can’t comment on any licensing required by 3rd parties to leverage platform authenticators. On your other question, you can configure WS1 Access to leverage Azure AD as 3rd Party IDP for authentication + MFA. Its important though that you configure TrueSSO with Horizon to avoid a subsequent password prompt.
LikeLike
Thanks a lot Steve, hopefully VMware will announce soon the support of this feature (passwordless) on WS1 on-premises. One question Steve, I imagine that considering a FIDO2 scenario within EUC (VDI / RDS) instances will not make much sense because once the access is validated, the rest of the authentications would be performed by SAML in federated environments, right?
Best regards,Steve
LikeLike
Using FIDO2 or Certificate Authentication still makes a lot of sense even in a federated environment. My personal preference is to perform certificate authentication along with Device Compliance if Workspace ONE UEM is managing the Win10/MacOS endpoint. You can also include Intelligent Hub MFA (cloud only) and Login Risk (cloud only) in the authentication.
LikeLike